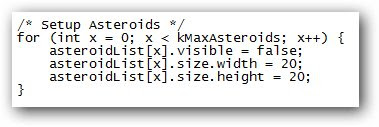
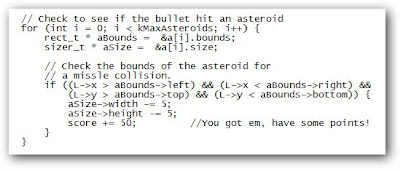
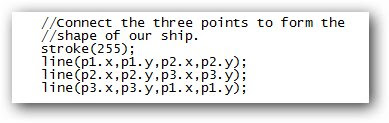
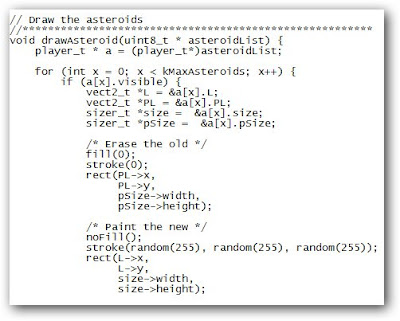
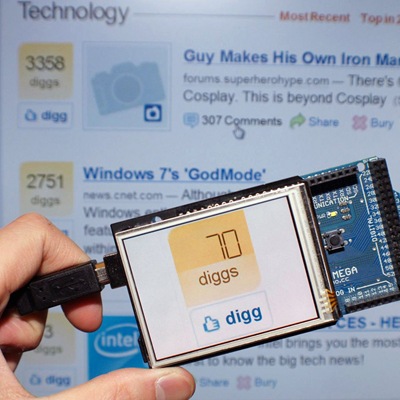
Last week, I wrote about a few gagdets that were open source, hackable down to the very circuit boards that make them up. True- any device is hackable at a fundamental level if a DIYer is willing to go there (even an iPod Nano). But there are some devices were made to be hacked, to be customized, and to be fully owned and used to the fullest.
That’s an interesting concept: a device is designed to be open source actually enhances the ownership and usability of the product. So what exactly does an open source hardware gadget offer, and why is it a good thing?
1. Customization = more happiness
Devices that are open source are more easily tailored to customize each user’s individual needs, whereas something that’s off the shelf and difficult to tweak usually results in some tradeoffs and compromises. So a well designed, open source hardware gadget that’s meant to be hacked will generally result in more users happier with the end product.
I was once told that the difference between a Mercedes and a Toyota is that with the Mercedes, “they really thought of everything when they designed it”. But what if they didn’t have to? What if there was no way they could think of everything, even if they tried?
In fact, it would probably be quite humbling for a Mercedes, a Samsung, or a Sony to admit that perhaps the customer might actually know what they want…and be able to design it better. So they’re even less likely to make the devices easy to modify. And if it’s not an issue of pride, there’s always one of liability with anything hardware.
2. Devices are less condescending (and less frustrating)
Many products, software or hardware, seem to be designed with the notion of idiotproofing in mind. A classic software example is with Windows Vista and User Account Controls. For those unfamiliar, it keeps asking you to confirm, any time you want to do something. Every time it asks you “are you really sure you want to do this?” it’s like a condescending jab suggesting that you’re a 90-year-old Grandma who’s never used a computer before (no offense, Grandma :)
I’m willing to live with the fact that if I break my computer, it’s my fault. I’m not going to blame anyone else. 
3. Learning by doing
People get to learn through hands-on hacking and tweaking.
I’m an avid overclocker, which for the sake of argument, I’ll consider a simple form of hardware hacking from a firmware level. I do my work in the BIOS, and if I’m working on the GPU, nVidia has a higher level tool for that, called nTune.
This wasn’t always the case, and I had to start from scratch. But wanting to create the most powerful computer my college student dollar could buy, I had to get creative, shop for deals, and get the compatible parts I could customize. Then I did a ton of research, put hours and hours into trial, error and testing, and walked away not only with the best computer for me with my budget, but also a skill set that I could use over and over again, and teach to others as well.
Since then, I’ve even overclocked my netbook, which presumably was never meant to be pushed to such limits. But the ability to do that makes me feel like the $400 I spent was *that* much more worth it.

4. Empowered, smarter users
Hackability and open source hardware encourages tinkering and learning by doing. Over time, this will create a group of bright, determined hackers, makers and DIYers excellent in the realm of problem-solving – and ready to teach others their trade.
In general, this makes people more inclined to figure things out and be more analytical, which could translate to folks being better at their day jobs- a more highly skilled and analytical technical workforce.
With respect to “innovation”, there are simply more qualified minds with more tools, and more people thinking about the best solution to a problem. This is excellent for businesses as well, since a growing number of companies realize that a lot of talent exists outside its four walls (see “not invented here”).
How does that translate to immediate, tangible sales? One school of thought suggests that the App Store was what made the iPhone successful, since more uses for the iPhone, intended or unintended, made it more worthwhile to own one. In fact, the ability to jailbreak the iPhone probably resulted in many many more sales of the hardware itself, not to mention the black market app stores that have arisen to create a niche industry in itself.
Hackability is valuable, both to businesses and consumers alike.
5. Stimulate the economy (really!)
All of this is fine and good, but I like to think that it can translate to an even broader phenomenon.
Self/community-taught users with access to open devices conducive to customization could lead to many things:
- rapid prototyping for product development (something the Arduino is used for a lot)
- businesses that sell aftermarket products and accessories (like Pimp my Ride for auto mods)
- consulting businesses designing custom solutions with easy-to-hack hardware
This ultimately leads to the creation of more products and more development by more people, not to mention that it could create more opportunities for folks to start businesses from their hobbies and self-taught expertise.
These are five big reasons why open source hardware gadgets are useful, and why we need more of them. Yes, closed source devices can be hacked to a similar effect. But rather than trying to shut down the hackers, open source welcomes it.
But everything else equal, are most people more interested in having something that looks nice, or having something that they can open up and mod to their heart’s content? Well, it depends on who’s buying. But how that product is ultimately used should be up to the person who spent the money to purchase it, and the more they can do with it, the more it’s worth to them.

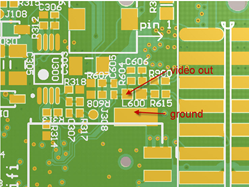
 While some of the schematics are available
While some of the schematics are available  This was especially interesting for me, since I wanted to overclock my
This was especially interesting for me, since I wanted to overclock my 
 Finally, OpenMoko’s
Finally, OpenMoko’s